Hashcat is a password recovery tool that has gained popularity for its wide range of supported hashing algorithms. It was initially a proprietary software but was later released as open source in 2015. Hashcat is available for Linux, OS X, and Windows operating systems. Some of the supported hashing algorithms include LM hashes, MD4, MD5, SHA-family, Unix Crypt formats, as well as algorithms used in MySQL and Cisco PIX.
To install Hashcat, you can visit the official website at Hashcat.net. There are two download options available, and for Windows users, it is recommended to choose the “hashcat binaries” option for easy installation. After downloading the compressed file, extract it to a specific directory.
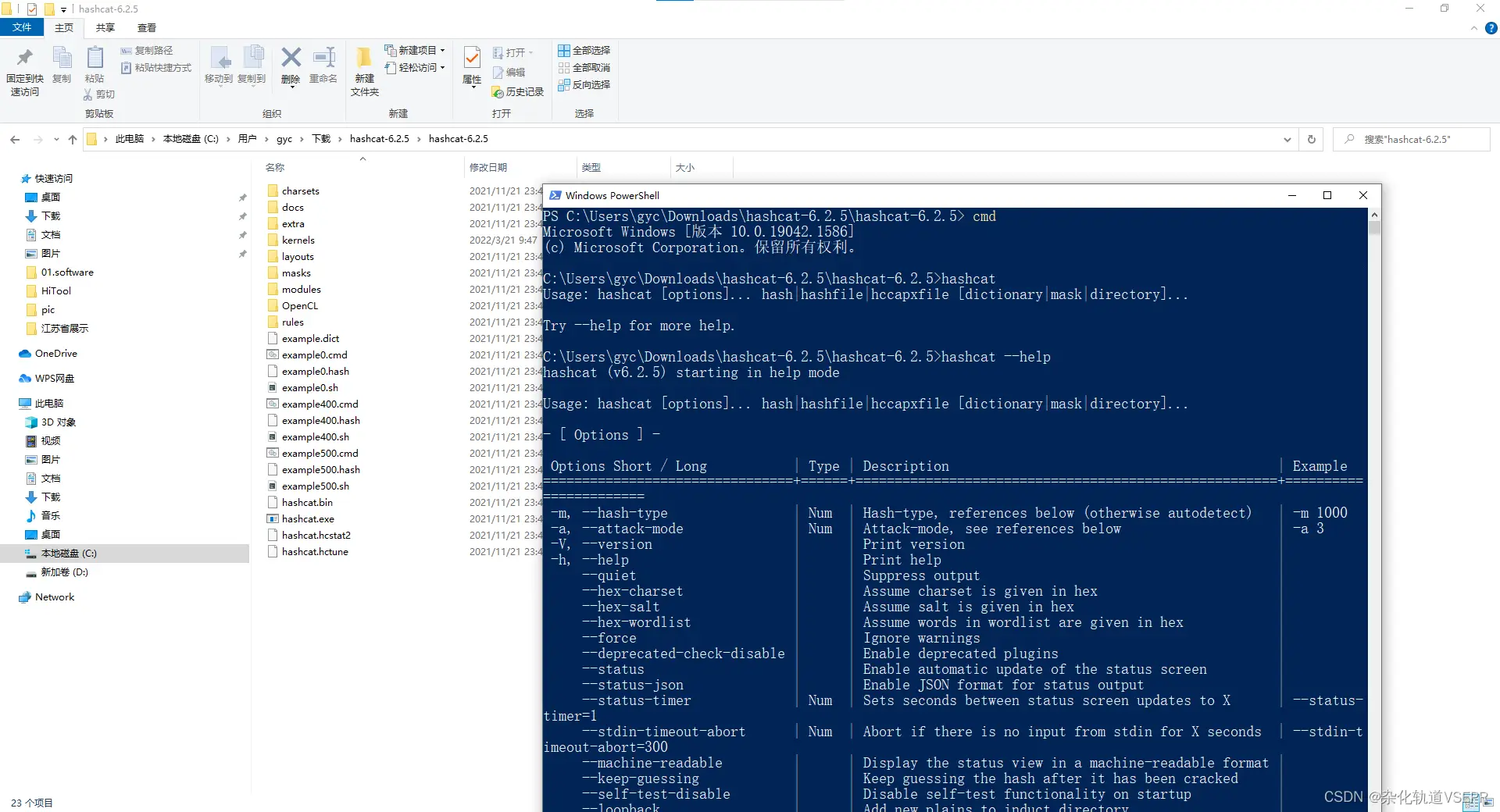
To run Hashcat, open the PowerShell in the extracted folder directory. Hold the Shift key and right-click the mouse, then select the “Run with PowerShell” option. You may encounter a warning message stating that Windows does not trust the path. In this case, you can use the “.\hashcat –help” command to view all available commands and their usage. The most commonly used commands can be found there, and you can refer to them as needed. Overall, Hashcat is a powerful software that is worth investing time to learn.
You can use the “.\hashcat -a” command to select the password cracking mode, followed by different parameters representing different cracking methods. For example:
- Brute Force Attack: This method involves trying all possible combinations until the correct password is found.
- Combination Attack: This method combines two lists of words to create different combinations for password cracking.
- Dictionary Attack: This method uses a pre-generated list of commonly used passwords, such as pet names, to crack passwords.
- Mask Attack: This method is similar to brute force attack, but with known details about the password, making it more precise.
You can choose the desired mode based on your requirements. The official Hashcat website provides detailed explanations for each mode, along with corresponding numeric codes.
In order to demonstrate the password cracking process, we need another software called “John the Ripper.” It works in conjunction with Hashcat by decrypting the ciphertext and then using Hashcat to convert it into plaintext. You can download John the Ripper from its official website.
To obtain the hash value using John the Ripper, open PowerShell in the John the Ripper folder directory. Then, run the necessary commands to extract the hash value. Copy the obtained hash value.
Next, use Hashcat to retrieve the plaintext password. Open PowerShell in the Hashcat directory and run the appropriate command. If you encounter any errors, it may be due to outdated CPU decryption. In that case, you can install CUDA tools for GPU acceleration.
If you face any issues related to CUDA versions, you can refer to the official Hashcat forum for solutions. Make sure to have the correct CUDA version installed, such as nvrtc641010.dll.
If you encounter any further difficulties, you can try decrypting a Word file instead. Run the John the Ripper and Hashcat commands accordingly, and save the hash value in a text file for future use.
In conclusion, Hashcat is a powerful password recovery tool with extensive capabilities. By following the appropriate steps and using additional software like John the Ripper, you can enhance your password cracking abilities. Remember to always use these tools responsibly and legally.
 量子哈希
量子哈希