0x00 Introduction
In the realm of internal network penetration testing, the initial step often involves gaining access to a web server through external reconnaissance and exploiting vulnerabilities to establish a foothold. Once inside the web server, the focus shifts to gathering information and launching attacks on other internal hosts, either through password-based attacks or exploiting vulnerabilities. While the concepts of internal networks, domains, domain controllers (DC), and Active Directory (AD) are not covered in detail here, it is recommended to research these topics for a better understanding. Practical tutorials on internal network penetration testing can be found in resources like Vulnstack (Part 1).
0x01 Information Gathering
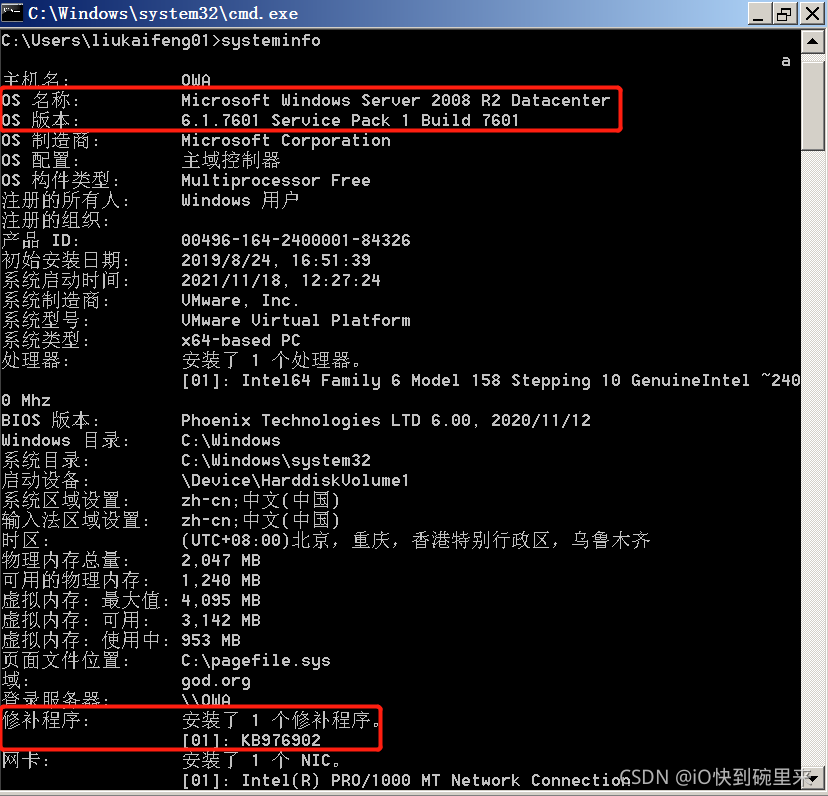
The first step in internal network penetration testing is to gather information about the target system, such as the operating system (OS) version and installed patches. This information can help identify potential vulnerabilities. The following commands can be used for information gathering:
systeminfo: View detailed system information, including OS version and patch installation status.net start: Check the list of running services to determine the role of the host in the domain.tasklist: View the list of running processes.netstat -ano: Check open ports on the host.net view /domain: Determine if a domain exists.ipconfig /all: View hostname, domain DNS, and IP information.net view: List all hosts in the domain.net time /domain: Check the domain server time, which can help identify the DC.nslookup: Retrieve the IP address of a domain name.net config workstation: View login information.whoami /all: Display user information.net user /domain: List domain users, which can be used as a dictionary for password cracking.
It is important to note that some commands may require executing them on the DC or enabling the RPC service on other domain hosts. Additionally, tools like nmap, masscan, empire, and nishang can also be used for probing live hosts within the domain.
0x02 IPC, SMB, and WMI
Internal network penetration testing heavily relies on password-based attacks. Since many domain members share passwords, gaining access to one host can provide opportunities to escalate privileges and expand the password dictionary for further attacks on other hosts within the domain. The SMB (Server Message Block) protocol and IPC (Inter-Process Communication) play crucial roles in this process.
SMB is a client/server protocol used for file and printer sharing, including named pipes used in IPC connections. IPC connections rely on the SMB protocol, and both require the opening of ports 139 and 445. The IPC$ share is particularly important for establishing connections and can be used for password cracking. The following commands demonstrate the usage of IPC and SMB:
net use: View current network connections.- Establishing an IPC connection with a remote host using the command:
net use \\192.168.52.143\IPC$ /user:godadministrator hongrisec@2021. - Copying files from the web server to the target host using the established IPC connection.
In addition to IPC and SMB, WMI (Windows Management Instrumentation) provides an interface for managing computers and executing system commands. It is widely used for remote administration. Various protocols and services, such as SSH (port 22), Telnet (port 23), RDP (port 3389), and RPC (port 135), are also relevant for remote management and communication.
0x03 at & schtasks
The at and schtasks commands are used to create scheduled tasks. The at command is applicable to Windows versions prior to Windows 2012, while schtasks is used in Windows 2012 and later versions. The following steps outline the usage of these commands:
- Establish an IPC connection to the target host with the provided credentials.
- Copy the desired command script to the target host.
- Check the target system time and create a scheduled task using
atorschtasksto execute the copied script. - Remove the IPC connection.
Commands such as net use and copy can be used to establish IPC connections and copy files, respectively.
0x04 smb & wmi
Similar to the previous methods, the psexec tool from the official Microsoft PSTools suite can be used for remote execution of commands. It does not require establishing an IPC connection explicitly. However, it should be noted that all these methods rely on IPC$ sharing and require ports 139 and 445 to be open. It is important to understand that these methods are essentially variations of the same approach, leveraging IPC$ sharing for password cracking and remote management.
Tools like impacket provide additional capabilities for passing hashes and executing system commands remotely. They can be used to establish connections and perform various attacks. However, caution should be exercised as these tools may be flagged by antivirus software.
0x05 pth, ptk & ptt
When it comes to password cracking, several techniques can be employed, including Pass-the-Hash (PTH), Pass-the-Key (PTK), and Pass-the-Ticket (PTT). These techniques allow for the movement and reuse of credentials without the need for plaintext passwords. It is worth noting that Windows systems after Vista and Windows Server systems after 2003 use NTLM Hash for authentication.
Tools like mimikatz can be used to obtain and exploit PTH and PTK. Additionally, hash cracking tools like hashcat can be employed to crack hashes and retrieve plaintext passwords.
PTT attacks involve leveraging the Kerberos protocol for authentication. By injecting fresh tickets into memory, attackers can bypass authentication and gain access to resources. Exploiting vulnerabilities or using tools like kekeo can facilitate PTT attacks.
It is important to mention that certain patches or configurations may prevent the retrieval of plaintext passwords. In such cases, alternative methods like hash passing or registry modifications can be explored.
0x06 Conclusion
Internal network penetration testing involves a series of steps, starting from gaining access to a web server and gradually expanding control over the domain. By leveraging various techniques, such as IPC, SMB, WMI, and password cracking, testers can navigate through the network, escalate privileges, and ultimately compromise the domain controller. It is crucial to adapt the approach based on the target environment and consider the limitations and security measures in place.
References:
- SQL Server Named Pipes and their usage
- Inter-Process Communication (IPC): Shared Memory and Message Queues
- Named Pipes, TCP/IP, and Anonymous Pipes
- Windows System Security: IPC$ Sharing and Other Shares (C$, D$, Admin$)
 量子哈希
量子哈希












