CDLinux is a highly practical Linux operating system that has gained popularity for its lightweight, fast, and efficient nature. Not only that, CDLinux also offers a certain level of security to help protect your computer and data. Today, we will introduce CDLinux Waterdrop Download, which allows you to conveniently use CDLinux and enjoy an efficient and secure user experience.
What is CDLinux Waterdrop Download?
CDLinux Waterdrop Download is a download tool specifically designed for the CDLinux system. It provides users with an intuitive and user-friendly graphical interface to easily search for and download the desired software. With CDLinux Waterdrop Download, users can conveniently and quickly obtain the software they need without the hassle of manually installing dependencies, saving a significant amount of time and effort.
Advantages of CDLinux Waterdrop Download
CDLinux Waterdrop Download offers the following advantages:
-
Convenience and ease of use: The interface of CDLinux Waterdrop Download is simple and intuitive, with easily accessible menu options. Users can quickly find the desired software by searching for keywords and then easily download it with the click of a button. For users who are not familiar with Linux commands, CDLinux Waterdrop Download is a very convenient tool.
-
Fast and efficient: CDLinux Waterdrop Download is incredibly fast, thanks to its use of multi-threaded download technology, which allows for simultaneous downloading of multiple files, reducing download time. Additionally, CDLinux Waterdrop Download can automatically install dependencies, eliminating the need for manual installation and saving time and effort for users.
-
Security and reliability: CDLinux Waterdrop Download originates from the official CDLinux repository, ensuring a high level of reliability and security. When downloading software using CDLinux Waterdrop Download, users do not have to worry about malicious software or virus infections, ensuring the security of their computer and data.
How to use CDLinux Waterdrop Download?
-
Open CDLinux Waterdrop Download: CDLinux Waterdrop Download can be opened either in the graphical interface or in the terminal. If opening in the terminal, simply enter the command “cdlget” to open CDLinux Waterdrop Download.
-
Search for the desired software: Enter the keywords for the software you want to download in the search box, such as Firefox or Chrome, and click the search button to find the desired software.
-
Download the desired software: Click on the software name, select the download version, and then click the “Download” button to start the download. If prompted for a sudo password during the download, enter it accordingly.
-
Install the software: Once the download is complete, CDLinux Waterdrop Download will automatically navigate to the software installation directory. Users simply need to double-click on the installation file and enter the sudo password to complete the installation.
CDLinux Waterdrop Download is a highly practical, convenient, fast, and secure software download tool designed for the CDLinux operating system. It allows users to conveniently obtain the software they need without worrying about malicious software or virus infections, ensuring the security of their computer and data. Therefore, when using the CDLinux operating system, it is recommended to use CDLinux Waterdrop Download to enhance your user experience with efficiency and security.
Related questions for further reading:
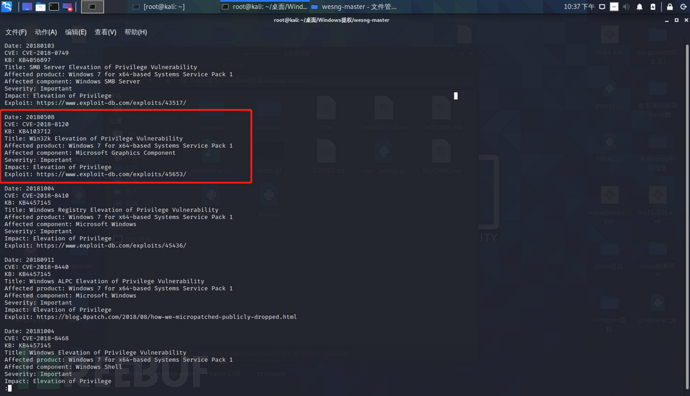
How to start Waterdrop cracking in CDLinux system via command line?
Waterdrop is a third-party GUI for Reaver and Aircrack. First, you need a wireless network card that supports monitoring and insert it into your computer. Then, start CDLinux with Waterdrop, open the terminal, and switch to root:
sudosu
Under root privileges, enable the monitoring mode of the network card:
airmon-ng start wlan0
Here, wlan0 is the device number of your wireless network card. If your device number is not wlan0, please make the necessary modifications. How to check the device number? It’s just a matter of looking for the device related to the network card under /dev. Search for methods online, as this is beyond the scope of this discussion.
Next, let’s see which network cards support PIN:
wash -i mon0 -C
If there are too many wireless SSIDs around, you can search by different channels. Add a parameter -c to the command line above, which is a number between 1 and 13, such as -c 6 to search on channel 6.
Once you have found your target SSID, use the following command to brute force the PIN:
reaver -i mon0 -b xx:xx:xx:xx:xx:xx -d 0 -vv -a -S -N
Here, xx:xx:xx:xx:xx:xx is the MAC address of the SSID.
What are some effective methods to crack WiFi passwords other than using a universal key?
First, let’s clarify that a universal key is not actually cracking the WiFi password. It simply records the names (SSID) and MAC addresses of different locations’ routers, along with their passwords. When you use software to automatically scan, the server will compare the WiFi networks around you with the stored database and fill in the password if there is a match. The universal key saves these passwords by either automatically uploading them through the software or by inducing users to share their WiFi information.
Now, let’s discuss how to crack WiFi passwords. The most effective method is using a dictionary attack, which involves trying different passwords one by one. However, this method can be time-consuming and challenging, especially for passwords with a combination of letters, numbers, and special characters. If the router has MAC address filtering enabled, even if you crack the password, you still won’t be able to connect.
There are various WiFi password cracking software available online, such as Phantom WiFi and Universal Key Crackers. However, it is important to note that cracking WiFi passwords without proper authorization is illegal in many jurisdictions. It is always recommended to use legal and ethical means to access WiFi networks.

02 The second method is more advanced and involves using a dictionary (a TXT document containing various possible passwords) to brute force the WiFi password. In other words, it involves trying each password one by one. However, there is a limitation in terms of speed and the router itself. Each time you enter a password and verify it with the router, it takes a considerable amount of time. You can overcome this limitation by using CDLinux or similar cracking software.
03 In essence, CDLinux and similar software are lightweight versions of Linux systems (Windows is not suitable for network packet capture due to its limitations). These systems use certain software to interrupt the connection between the client and the router. Nowadays, WiFi devices are designed to automatically reconnect after a disconnection. During the automatic reconnection process, the device will send the encrypted WiFi password to the router. Upon receiving this information, the router will compare it with the internally stored WiFi password, which has undergone the same encryption process. If they match, authentication is successful.
04 These software tools capture the data packets containing the encrypted password. Since WiFi passwords are encrypted using one-way encryption, which means they can only be encrypted and not decrypted (similar to solving N equations with one unknown, where you can find multiple solutions for a given Y value, but for a given X value, there is only one corresponding Y value), we usually encrypt the password data in the dictionary and compare it with the captured data packets. If they match, we have found the password. This method depends on the speed of your computer’s CPU and GPU, and can achieve cracking speeds of several thousand attempts per second.
05 PIN cracking has become a popular method for cracking WiFi passwords in recent years. But what is a PIN? What is its purpose? Let’s start with the concept of WPS. WPS (WiFi Protected Setup) is a recommended wireless configuration protocol that allows devices supporting WPS to automatically establish a connection without manually entering the SSID and password. While convenient, it also poses a security risk. If we know the PIN of a router, we can openly connect to the WiFi network without knowing the actual password. Once we know the PIN, the WPA2 encryption becomes ineffective, and we can use software like Reaver to retrieve the password.
06 The PIN is a simple eight-digit decimal number, with the last digit (the eighth digit) being a checksum (which can be calculated based on the first seven digits). During verification, the first four digits are checked. If they match, a message is returned. Therefore, you only need to try 10,000 combinations for the first four digits. Once the first four digits are determined, you only need to try 1,000 combinations (the next three digits). The checksum can be calculated based on the first seven digits, allowing us to brute force the PIN. So even if you don’t know how to calculate the checksum, you can try a maximum of 10,000 + 1,000 + 10 attempts, which is 11,010 attempts to obtain the PIN and thus the WiFi password. Isn’t it much simpler?
It is important to note that cracking WiFi passwords without proper authorization is illegal and unethical. It is always recommended to use legal and ethical means to access WiFi networks.
 量子哈希
量子哈希