-h/--help:显示联机帮助
-m/--hash-type:Hash类型,比如:md4(900),md5(0),SAH-1(100),SHA-512(1700)等等。
-v/--version:打印系统的版本信息
--quite:
-a/--attack-mode:破译模式,包括直接攻击模式(0),组合模式(1),大小写转换(2),暴力破解攻击(3)等等。(举例:-a 0)
-o/--outfile:定义文件运行输出的文件
-b/--benchmark:运行测试
--remove:把破译出的密码从密码列表中移除。
Hashcat is an open-source software that performs fast password cracking using GPUs. The latest version available on the official website is hashcat 4.1.0. Versions 3.00 and later can be found on the website. Hashcat is considered the fastest and most advanced password recovery tool in the world. With a good password dictionary, it is possible to crack over 90% of passwords from a large password list. The current latest version of Hashcat is 4.1.0, which combines the CPU-based hashcat (now called hashcat-legacy) and the GPU-based oclHashcat. During installation, it automatically generates a multi-threaded version of hashcat or an ocl version based on the hardware of the machine. To install hashcat, you can download the source code from the website. Hashcat was developed in 2009. Before hashcat, there were already tools like “PasswordPro” and “John The Ripper” that were close to perfection. However, for unknown reasons, these two tools did not support multi-threading. This led to the development of hashcat, which utilizes multiple cores of modern CPUs for computation. It is important to note that hashcat is not 100% accurate in password cracking. John the Ripper can also support MPI through patches, but it can only be used for brute-force attacks and does not have suitable methods for cracking MD5 using rule-based attacks with MPI support. The first version of hashcat was called “atomcrack.” It was simple and had limited functionality, but its MD5 core was multi-threaded. Atomcrack only used basic dictionary attacks to crack MD5, but it was very fast. Over time, more algorithm types, a dictionary variant rule engine, a Windows version, and different attack modes were added to hashcat. These developments took about six months and were completely non-public. In version 0.29, “atomcrack” was renamed to “Dr.Hash.” It was not until December 24, 2009, with the release of the official version hashcat 0.30, that it was officially renamed “hashcat.” Hashcat 0.40 was released on August 5, 2012, which added Mac OS X binaries. This version gradually evolved into the hashcat we use today. Another component of Hashcat is oclHashcat, which is a GPGPU-based multi-hash cracking program. Its features include brute-force attacks, combination attacks, dictionary attacks, mask attacks, and rule-based attacks. oclHashcat is a fusion of oclHashcat-plus and oclHashcat-lite, both of which are powerful components that have been deprecated. The main issue with oclHashcat is its architecture. It is designed for Combinator attacks and is efficient for fast algorithms, but it becomes inefficient when combined with slow algorithms. This is why many people still prefer to use the CPU-based hashcat, as it can perform simple dictionary attacks. To perform dictionary attacks on the GPU, the algorithm issue of oclHashcat needs to be addressed. This led to the creation of a new method called oclHashcat-plus. During this process, the developers of oclHashcat introduced a specialized GPU cracker called oclHashcat-lite, which focuses on mask attacks and brute-force attacks for individual hash values. To provide users with fewer limitations, oclHashcat-lite can coexist with oclHashcat-plus. Dictionary attacks on the GPU are effective for fast algorithms like MD4 and MD5, but the efficiency is not as high because uploading the wordlist to the GPU takes more time. Therefore, attacking these fast algorithms on the CPU is sufficient. However, for slow algorithms like md5crypt and phpass, the GPU’s processing speed is much faster. This is because these algorithms are designed to reduce their vulnerability to collision attacks. On December 6, 2013, oclHashcat 1.00 was released, claiming to combine the advantages of oclHashcat-lite and some features of oclHashcat-plus. For certain types of hash values, the cracking speed of oclHashcat 1.00 is comparable to oclHashcat-lite, or even faster. From version 1.00 onwards, oclHashcat replaced the functionalities of oclHashcat-lite and oclHashcat-plus. Another major feature of oclHashcat is its GPU-based rule engine, which allows rule-based attacks. The fast algorithm utilizes the GPU-based rule engine to improve GPU utilization. With this strategy, even simple dictionary attacks on the GPU become efficient. The rule engine on the GPU is very fast, and depending on the rules themselves, it can achieve almost the same speed as the combinator attack in oclHashcat. This is a unique feature that sets it apart from other hash crackers. The slow algorithm utilizes the CPU-based rule engine to increase the size of the wordlist. This allows for attacks with very small dictionaries. These small dictionaries are actually expanded in memory by the rule engine. This way, the time required to store the wordlist on the GPU can be ignored. Through these developments, oclHashcat became somewhat similar to the CPU-based hashcat. The basic commands and usage of hashcat can be further analyzed with examples in future articles. Using Hashcat with the -a 0 option, we can try password matching with a small dictionary in Kali, which comes with hashcat pre-installed. This allows us to experience the functionality of hashcat. We can use the Top109Million dictionary to match passwords in the password.txt file and output the matched results to the outfile file. The -o command writes the cracked passwords and their corresponding plaintext directly to the outfile file. The –remove command filters out passwords that have not been cracked yet and removes them from the password list. During the experiment, I encountered a small issue. Normally, the -o command should output the matched passwords to the outfile file, but in my case, the outfile file was not generated in the specified path. This is because hashcat caches the cracked results in the potfile during the password cracking process. When encountering the same password list in the future, hashcat retrieves the results directly from the potfile. The cracked passwords and their corresponding results are stored in the potfile. This can be disabled using the –potfile-disable command. In addition to using a single dictionary for password cracking, hashcat can also perform combination attacks between dictionaries and rule-based attacks. However, due to limitations in the virtual machine environment, the performance was not ideal. Therefore, I configured hashcat on my local Linux system to crack passwords using the GPU. If you are interested, I can share the installation process of hashcat and the challenges I encountered next time.
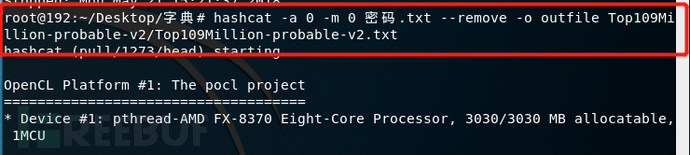
When it comes to command usage, we can analyze it in more detail with examples in future articles. In Kali, hashcat is pre-installed, so we can try password matching with a small dictionary to experience the functionality of hashcat. We can use the Top109Million dictionary to match passwords in the password.txt file and output the matched results to the outfile file. By using the -o command, the cracked passwords and their corresponding plaintext will be directly written to the outfile file. The –remove command will filter out passwords that have not been cracked yet and remove them from the password list.
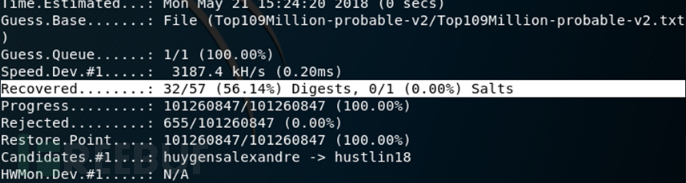
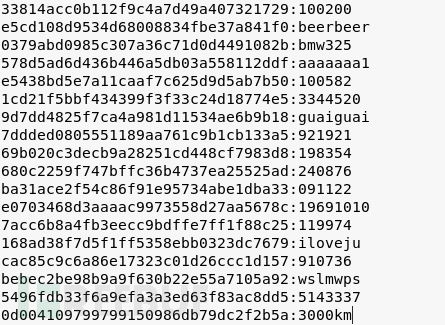
During the experiment, I encountered a small issue. Normally, the -o command should output the matched passwords to the outfile file, but in my case, the outfile file was not generated in the specified path. This is because hashcat caches the cracked results in the potfile during the password cracking process. When encountering the same password list in the future, hashcat retrieves the results directly from the potfile. The cracked passwords and their corresponding results are stored in the potfile. This can be disabled using the –potfile-disable command.
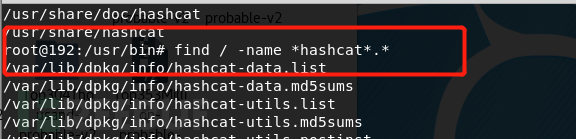
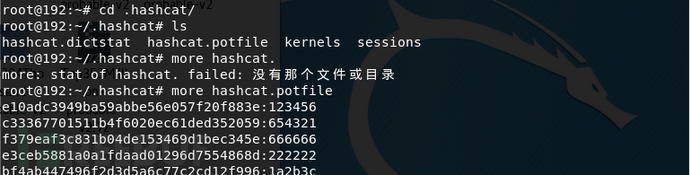
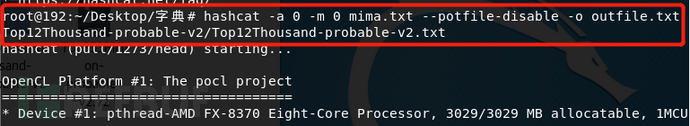
In the potfile, the cracked passwords and their corresponding results are stored. By using the –potfile-disable command, this behavior can be changed. In addition to using a single dictionary for password cracking, hashcat can also perform combination attacks between dictionaries and rule-based attacks. However, due to limitations in the virtual machine environment, the performance was not ideal. Therefore, I configured hashcat on my local Linux system to crack passwords using the GPU. If you are interested, I can share the installation process of hashcat and the challenges I encountered next time.
 量子哈希
量子哈希